
Phishing: what it is and how to stop it
Phishing is a cyber attack that uses disguised email as a weapon. The goal is to trick the email recipient into believing that the message is something they want or need – a request from their bank, for instance, or a note from someone in their company – and to click a link or download an attachment.
What really distinguishes phishing is the form the message takes: the attackers masquerade as a trusted entity of some kind, often a real or plausibly real person, or a company the victim might do business with. It is one of the oldest types of cyberattacks, dating back to the 1990s, and it is still one of the most widespread and pernicious, with phishing messages and techniques becoming increasingly sophisticated.
‘Phish’ is pronounced just like it is spelled, which is to say like the word ‘fish’ – the analogy is of an angler throwing a baited hook out there (the phishing email) and hoping you bite. The term arose in the mid-1990s among hackers aiming to trick AOL users into giving up their login information. The ‘ph’ is part of a tradition of whimsical hacker spelling, and was probably influenced by the term ‘phreaking,’ short for ‘phone phreaking,’ an early form of hacking that involved playing sound tones into telephone handsets to get free phone calls.
Nearly a third of all breaches in the past year involved phishing, according to the 2019 Verizon Data Breach Investigations Report. For cyber-espionage attacks, that number jumps to 78%. The worst phishing news for 2019 is that its perpetrators are getting much, much better at it thanks to well-produced, off-the-shelf tools and templates.
Some phishing scams have succeeded well enough to make waves:
- Perhaps one of the most consequential phishing attacks in history happened in 2016, when hackers managed to get Hillary Clinton campaign chair John Podesta to offer up his Gmail password
- The ‘fappening’ attack, in which intimate photos of a number of celebrities were made public, was originally thought to be a result of insecurity on Apple’s iCloud servers, but was in fact the product of a number of successful phishing attempts
- In 2016, employees at the University of Kansas responded to a phishing e-mail and handed over access to their paycheck deposit information, resulting in them losing pay
What is a phishing kit?
The availability of phishing kits makes it easy for cyber criminals, even those with minimal technical skills, to launch phishing campaigns. A phishing kit bundles phishing website resources and tools that need only be installed on a server. Once installed, all the attacker needs to do is send out e-mails to potential victims. Phishing kits as well as mailing lists are available on the Dark Web. A couple of sites, Phishtank and OpenPhish, keep crowd-sourced lists of known phishing kits.
Some phishing kits allow attackers to spoof trusted brands, increasing the chances of someone clicking on a fraudulent link. Akamai’s research provided in its Phishing–Baiting the Hook report found 62 kit variants for Microsoft, 14 for PayPal, seven for DHL, and 11 for Dropbox.
The Duo Labs report, Phish in a Barrel, includes an analysis of phishing kit reuse. Of the 3,200 phishing kits that Duo discovered, 900 (27%) were found on more than one host. That number might actually be higher, however. “Why don’t we see a higher percentage of kit reuse? Perhaps because we were measuring based on the SHA1 hash of the kit contents. A single change to just one file in the kit would appear as two separate kits even when they are otherwise identical,” said Jordan Wright, a senior R&D engineer at Duo and the report’s author.

Analysing phishing kits allows security teams to track who is using them. “One of the most useful things we can learn from analysing phishing kits is where credentials are being sent. By tracking e-mail addresses found in phishing kits, we can correlate actors to specific campaigns and even specific kits,” said Wright in the report. “It gets even better. Not only can we see where credentials are sent, but we also see where credentials claim to be sent from. Creators of phishing kits commonly use the ‘from’ header like a signing card, letting us find multiple kits created by the same author.”
Types of phishing
If there is a common denominator among phishing attacks, it is the disguise. The attackers spoof their e-mail address so it looks like it is coming from someone else, set up fake websites that look like ones the victim trusts, and use foreign character sets to disguise URLs.
That said, there are a variety of techniques that fall under the umbrella of phishing. There are a couple of different ways to break attacks down into categories. One is by the purpose of the phishing attempt. Generally, a phishing campaign tries to get the victim to do one of two things: handing over sensitive information and download malware.
Hand over sensitive information
These messages aim to trick the user into revealing important data – often a username and password that the attacker can use to breach a system or account. The classic version of this scam involves sending out an e-mail tailored to look like a message from a major bank. By spamming out the message to millions of people, the attackers ensure that at least some of the recipients will be customers of that bank. The victim clicks on a link in the message and is taken to a malicious site designed to resemble the bank’s webpage, and then hopefully enters their username and password. The attacker can now access the victim’s account.
Download malware
Like a lot of spam, these types of phishing e-mails aim to get the victim to infect their own computer with malware. Often the messages are ‘soft targeted’ – they might be sent to an HR staffer with an attachment that purports to be a job seeker’s resume, for instance. These attachments are often .zip files, or Microsoft Office documents with malicious embedded code. The most common form of malicious code is ransomware – in 2017 it was estimated that 93% of phishing e-mails contained ransomware attachments.
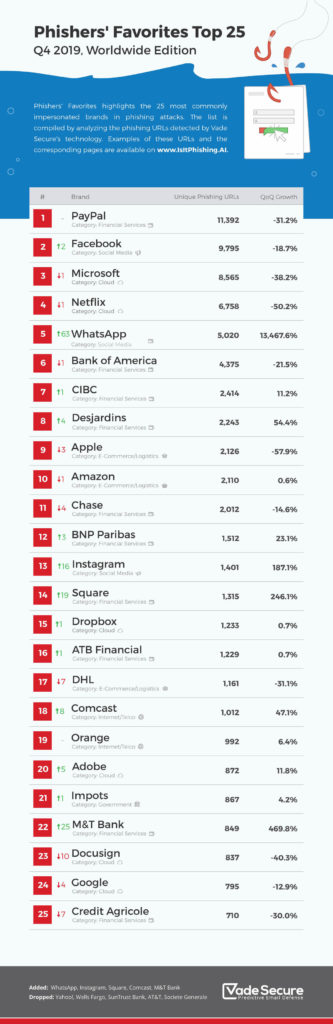
There are also several different ways that phishing e-mails can be targeted. As we noted, sometimes they are not targeted at all; e-mails are sent to millions of potential victims to try to trick them into logging in to fake versions of very popular websites. Vade Secure has tallied the most popular brands that hackers use in their phishing attempts (see infographic below). Other times, attackers might send ‘soft targeted’ e-mails at someone playing a particular role in an organisation, even if they do not know anything about them personally.
But some phishing attacks aim to get login information from, or infect the computers of, specific people. Attackers dedicate much more energy to tricking those victims, who have been selected because the potential rewards are quite high.
Spear phishing
When attackers try to craft a message to appeal to a specific individual, that is called ‘spear phishing’. (The image is of a fisherman aiming for one specific fish, rather than just casting a baited hook in the water to see who bites.) Phishers identify their targets (sometimes using information on sites like LinkedIn) and use spoofed addresses to send e-mails that could plausibly look like they are coming from co-workers. For instance, the spear phisher might target someone in the finance department and pretend to be the victim’s manager requesting a large bank transfer on short notice.
Whaling
‘Whale phishing’, or ‘whaling’, is a form of spear phishing aimed at the very big fish – CEOs or other high-value targets. Many of these scams target company board members, who are considered particularly vulnerable: they have a great deal of authority within a company, but since they are not full-time employees, they often use personal e-mail addresses for business-related correspondence, which does not have the protections offered by corporate e-mail.
Gathering enough information to trick a high-value target might take time, but it can have a surprisingly high payoff. In 2008, cybercriminals targeted corporate CEOs with e-mails that claimed to have FBI subpoenas attached. In fact, they downloaded keyloggers onto the executives’ computers – and the scammers’ success rate was 10%, snagging almost 2,000 victims.
Other types of phishing include clone phishing, vishing, snowshoeing. This article explains the differences between the various types of phishing attacks.
How to prevent phishing
The best way to learn to spot phishing emails is to study examples captured in the wild. This webinar from Cyren starts with a look at a real live phishing website, masquerading as a PayPal login, tempting victims hand over their credentials. Check out the first minute or so of the video to see the tell tale signs of a phishing website.
More examples can be found on a website maintained by Lehigh University’s technology services department where they keep a gallery of recent phishing e-mails received by students and staff.
There also are a number of steps you can take and mindsets you should get into that will keep you from becoming a phishing statistic, including:
- Always check the spelling of the URLs in e-mail links before you click or enter sensitive information
- Watch out for URL redirects, where you are subtly sent to a different website with identical design
- If you receive an e-mail from a source you know but it seems suspicious, contact that source with a new e-mail, rather than just hitting reply
- Do not post personal data, like your birthday, vacation plans, or your address or phone number, publicly on social media
If you work in your company’s IT security department, you can implement proactive measures to protect the organisation, including:
- ‘Sandboxing’ inbound e-mail, checking the safety of each link a user clicks
- Inspecting and analysing Web traffic
- Pen-testing your organisation to find weak spots and use the results to educate employees
- Rewarding good behaviour, perhaps by showcasing a ‘catch of the day’ if someone spots a phishing e-mail
IDG News Service






Subscribers 0
Fans 0
Followers 0
Followers