The massive ransomware attack, that has affected countries across the globe, may well be exacerbated this morning as employees return to work and open up emails with the malware attached.
The ransomware, also known as WannaCry, works by leveraging a Windows vulnerability that came to light last month when a cache of mysterious hacking tools was leaked on the Internet.
The tools, which security researchers suspect came from the NSA, include an exploit codenamed EternalBlue that makes hijacking older Windows systems easy. It specifically targets the Server Message Block (SMB) protocol in Windows, which is used for file-sharing purposes.
Patches
Microsoft has already patched the vulnerability, but only for newer Windows systems. However, due to the extent of problems, Redmond has now issued a patch for XP, Server 2003 and Windows 8.
That may have painted a giant bulls-eye for hackers to target these systems. The developer of Wanna Decryptor appears to have added the suspected NSA hacking tools to the ransomware’s code, said Matthew Hickey, the director of security provider Hacker House, in an email.
Security firm Avast said it has detected the ransomware, largely attacking Russia, Ukraine and Taiwan.
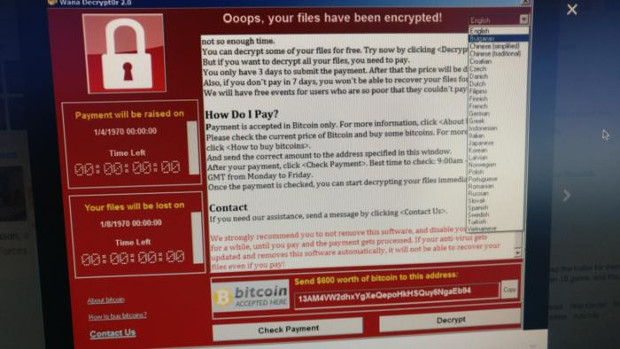
The Wanna Decryptor ransomware strikes by encrypting all the files on an infected PC, along with any other systems on the network the PC is attached to. It then demands a ransom of about $300 to $600 (€247-547) in bitcoin to release the files, threatening to delete them after a set period of days if the amount is not paid.
Security experts are urging organisations to patch vulnerable systems, upgrading to the latest versions of OSes, and making back-ups of any critical files.
URL stop
Another security research firm, MalwareTech, has created a page monitoring the attacks. The firm also found that a URL check performed by the malware as part of a test to see if it was running in a sandbox environment, provided a temporary block to its spread. The malware used a nonsense URL to check if it was running in the kind of test environment a researcher might use to safely probe its capabilities. In this instance, the malware would cease its activities. The URL was then registered so that even if the malware landed on a legitimate host, the check would stop its actions.
The malware is now suspected to have hit more than 100 countries, with an estimated 75,000 or so endpoints affected.
Among the infected hosts have been various verticals, such as utilities and healthcare, with the UK’s NHS being particularly badly hit.
HSE response
Here, the CIO of the HSE was reassuring the public that defences were in place and that vigilance was necessary to remain safe.
A statement on the HSE’s web site said:
“Following a decision by HSE’s Leadership last evening (12/05/2017) to remove all external access to the HSE IT Network, access to external email has been removed from all threatened and targeted devices. There are approximately 1,500 devices that are considered either threatened or targeted devices. This includes devices that deliver diagnostic imaging (NIMIS) and Bio-Medical Device control machines.”
“Overnight, the HSE’s Office of the CIO has been working closely with the organisations that deliver technology to the health system regarding assurance and levels of preparedness for this recent cyber-attack. Anti-Virus updates are currently being installed in these devices and a process of testing is underway. As there are approximately 1,500 devices it is expected that this process will take a number of days to complete.”
HSE staff were warned as they returned to work on Monday morning to be extra vigilant regarding the phishing emails and not to click on anything of there was the slightest doubt.
The executive has confirmed this morning via a tweet that it will keep its network isolated for a further 48 hours a s precautionary measure.
UPDATE: The Independent is reporting that three Irish hospitals have been hit by the ransomware. The story online says that around 20 machines were infected but were isolated before the malware could spread.
UPDATE: HSE CIO Richard Corbridge has confirmed that during its mitigation measures against WannaCry, the executive found the 20 odd machines that had an infection, but were not hit by the ransomware. An older virus was found and eliminated, Corbridge confirmed, but no machines appear to have fallen prey to WannaCry.
Nature of attack
The nature of the attack has prompted widespread speculation as to who might be behind it.
The rather modest nature of the ransom, with some estimates that the entire haul may only yet be in the tens of thousands of dollars, certainly no more than the hundreds, would suggest that this is not an entirely mercenary gambit.
Paul C Dwyer of Cyber Risk International said in the blog post that it may well be ‘shot across the bows, type attack by a nation state, or its proxies, to demonstrate the extent of potential cyberwarfare attacks.
“This has all the hallmarks of a “shot across the bow” in cyber warfare terms. The campaign was executed with “military” precision,” said Dwyer.
For anyone looking for information on combatting ransomware, a Europol resource at https://www.nomoreransom.org/ has a range of information and techniques.
IDGNS and TechCentral Reporters







Subscribers 0
Fans 0
Followers 0
Followers