
Protect yourself against ransomware with Rubrik’s fully-encrypted lifecycle management
In association with Rubrik
Rubrik applies and utilises encryption throughout the entire backup and recovery process, from ingest to restore. Whether data is local to the cluster or exists within the cloud, customers can be rest assured that their data, both at rest and in-flight, is encrypted and safe from ransomware and other malicious attacks.
Keeping your data safe from ransomware
Encryption is a process in which data is encoded in order to ensure it’s hidden or inaccessible to unauthorised users and devices. With ransomware and malicious threats on the rise, it’s essential that organizations ensure that their most valuable assets and sensitive data are encrypted and hidden away from bad actors. When we shift the conversation from production to backup data, it’s essential that encryption be applied everywhere. Data management solutions such as Rubrik become a global catalogue containing point-in-time copies of all of your production data, making encryption even more important than ever. At Rubrik, we take a ‘security first’ approach during our design, ensuring data is fully encrypted and, at the same time, providing an immutable file system to ensure that once data is written, it can never be changed. These principles help ease concerns since an organisation’s backups can always be used as their last line of defense. Rubrik’s encryption can be broken down into two different data buckets: ‘data at rest’ and ‘data in flight’
encrypting data at rest, everywhere.
Data at rest encryption (DARE) is a key strategy in deploying a defence in depth approach in the security world. DARE, along with Rubrik zero trust data management and immutable file system provide the groundwork for ensuring our customers are able to recover from nearly any cyber threat, while at the same time ensuring their data is always safe and hidden away from prying eyes. When it comes to encrypting data at rest, Rubrik provides a couple options: software encryption and hardware encryption.
Software encryption
Rubrik software encryption for data at rest works on the application level, meaning all the work and encryption is performed through software. As data is ingested, Rubrik generates a unique one-time only symmetric data encryption key (DEK). DEKs utilise the AES-256 cipher and are utilised to encrypt both the ingested backup data, along with any associated metadata generated by Rubrik. This process ensures that – without the associated DEK – the data is essentially unreadable, even by the Rubrik platform. This results in the need to store this associated DEK somewhere alongside the data itself.
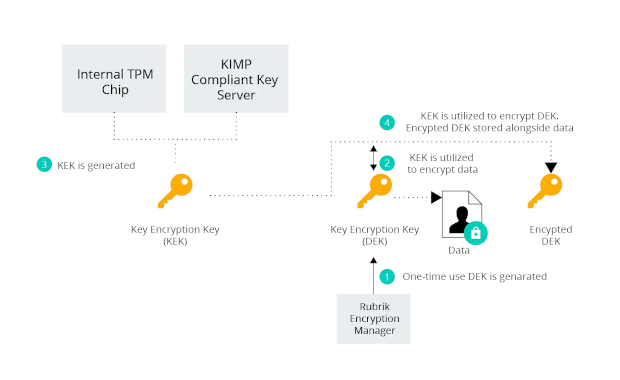
While storing the generated DEK locally is an option, it does present a security risk as anyone with the DEK could potentially decrypt the data. To combat this, Rubrik leverages a technique known as envelope encryption. When the initial encryption process with the DEK has been completed, Rubrik will then encrypt the DEK with another key called a key encryption key (KEK). The encrypted DEK is then stored alongside the ciphertext data, while any plaintext versions of it are immediately purged from memory. Therefore when Rubrik needs to read this data, it must pass through two phases of encryption, first decrypting the DEK with a KEK, then decrypting the data itself. To obtain and manage KEKs, customers can leverage either the internal trusted platform module (TPM) chip within the Rubrik appliance, or utilise an external key management interoperability protocol (KMIP) compliant key management server such as those provided by Hytrust or Cryptsoft.
In both cases, Rubrik adopts security best practices by allowing customers to easily perform key rotation on their KEKs through either the UI or the RESTful API.
Hardware encryption
Often public sector agencies face the challenge of protecting growing amounts of sensitive data and are under strict regulations when it comes to encryption. To address these challenges Rubrik also offers platforms elevated to the highest level of protection with FIPS 140-2 Level 2 validated self encrypting hard disk and solid state drives.
Hardware encryption works much in the same way as software encryption, but rather than Rubrik performing the encryption of the data within software, the self-encrypting drives utilise drive firmware to perform the encryption. Each self-encrypting drive utilises a password in order to generate it’s DEKs, and the DEKs never hit the memory space at all. These passwords, much like the Rubrik-generated DEKs, are further encrypted by a KEK, again, managed through an internal TMP or external KIMP compliant key management server.
Encrypting data in flight
While encryption at rest often gets the spotlight, it’s just as important that all data in flight is encrypted as well. Whether it be to prevent man-in-the-middle attacks, packet sniffers, or overall malicious activity, it’s crucial that encryption be applied to data as it traverses the network. This importance is further solidified when dealing with a data management solution such as Rubrik. As you can imagine, a data management solution, well, manages data – and this involves not only becoming a central repository for all of your production data, but moving this data around by performing tasks to support features such as long term archival and replication.
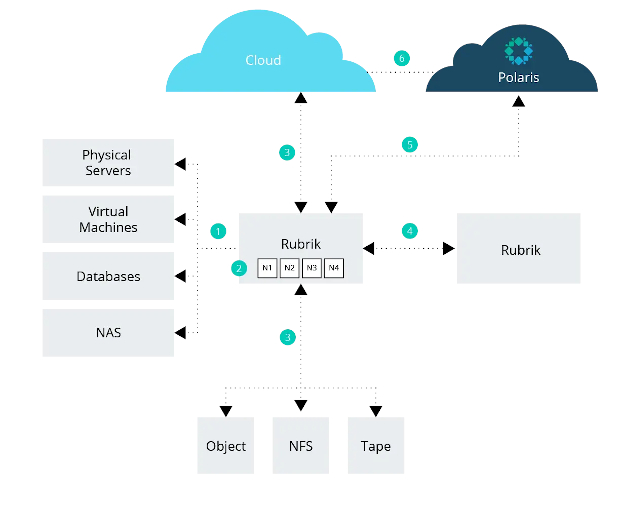
As shown above, we can see all of the external and internal communications between protected objects, the on-premises Rubrik platform, the cloud, and Rubrik Polaris. All communication in and out of the Rubrik platform is encrypted as follows:
- Communication between protected environments and Rubrik is fully encrypted. Communication to and from VMware vSphere environments utilises the NBDSSL protocol, while communication to and from other protected sources is encrypted via TLS.
- Aside from ensuring every internode request is authorised and authenticated, all communication within the Rubrik cluster from node to node is encrypted via TLS, contributing the ‘trust nothing’ approach of a zero-trust architecture
- When data is archived, whether to a public cloud storage provider or to an on-premises object store, network file system, or tape target, it is fully encrypted via TLS during the transfer. The data itself is also encrypted at rest, no matter the location.
- When leveraging Rubrik replication capabilities to replicate data to another Rubrik cluster for disaster recovery purposes, all communication between the clusters is completely encrypted via TLS
- Rubrik Polaris, a SaaS-based offering communicates with the on-premises Rubrik instance to provide multi-cluster management as well as a number of value-add services for customers. This communication is completely encrypted via TLS
- Many SaaS offerings around cloud-native protection within Rubrik Polaris also need to communicate with customer cloud environments. All communication between Rubrik Polaris and a customer cloud account is encrypted via TLS.
Furthermore, any requests made to the Rubrik platform, either through the UI or a RESTful API endpoint must be authenticated and authorised and are fully encrypted via TLS.
Rubrik is dedicated to providing end-to-end security no matter where your data resides. All data in flight is encrypted, and any data landing within the Rubrik platform, including archive locations, is encrypted at rest. But encryption isn’t the only safeguard Rubrik takes to give customers peace of mind.
The entire software stack is built around the idea of zero trust data management, trusting nothing by default, providing role-based access control, supporting multi-factor authentication, all backed by a distributed, immutable filesystem. To learn more about Rubrik’s Zero Trust Data Management architecture visit this solutions page.
Mike Preston, Rubrik







Subscribers 0
Fans 0
Followers 0
Followers