
Hackers can steal Windows credentials via links in Zoom chat
An unpatched vulnerability within Zoom allows an attacker to drop a malicious link into a chat window and use it to steal a Windows password, according to reports.
A hacker could use an attack known as a UNC path injection to expose credentials, according to an attack posted on Twitter and subsequently followed up with an additional video. According to The Hacker News, that is because Windows exposes a user’s login name and password to a remote server when attempting to connect to it and download a file.
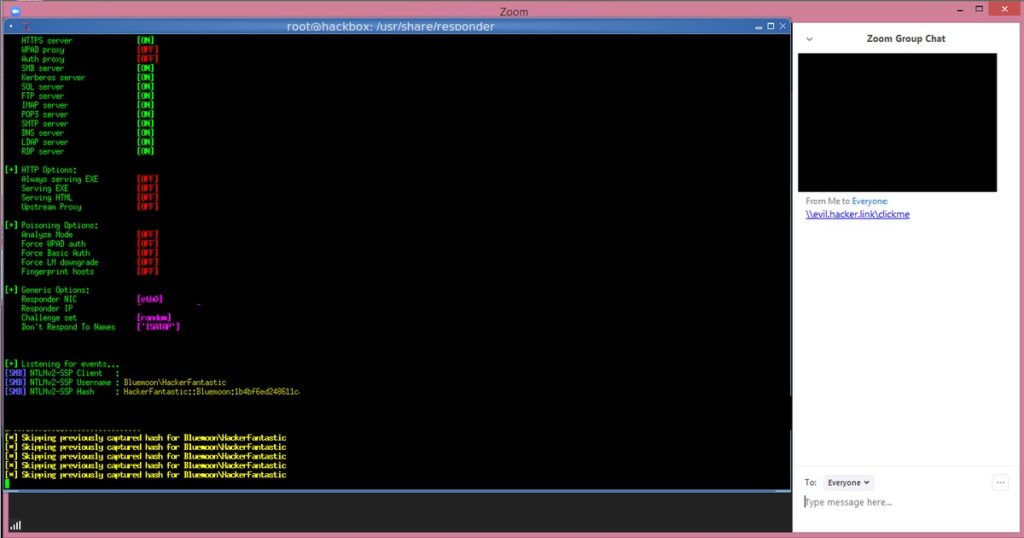
All an attacker needs to do is to send a link to another user and convince them to click it, for the attack to commence. Though the Windows password is still encrypted, the hack claims it can be easily decrypted by third-party tools if the password is a weak one.
As Zoom gains in popularity, it has caught the eye of the security community, which is more closely examining the videoconferencing software for weaknesses. In addition to the risk of ‘Zoom bombing,’ criticisms have been levelled at the software for claiming to be end-to-end encrypted, when in fact it actually is not. Last year, a flaw surfaced that potentially would allow remote users to join a Mac user to a call, then turn their camera on without permission. That flaw was patched. Zoom has not, however, announced a fix for the current bug.
The Hacker News recommended either using the Windows security policy settings to turn off the automatic transmission of NTML credentials to a remote server, or else just use the Zoom client for the Web.
IDG News Service







Subscribers 0
Fans 0
Followers 0
Followers